Meanwhile I think I’ve felt in love with Androguard. I love its Pythonic way handling things and its visualizations features. As many of you have noticed, you can run Androguard inside a Docker container. I’ve never used Docker before so it was about time. You can find some general information about the installation process on Arch Linux at this address.
Extensions
|
|
Installed diagmagic.py. To use it, type:
%load_ext diagmagic
The diagmagic extension is already loaded. To reload it, use:
%reload_ext diagmagic
On my main pentest machine (kudoz to @blackarch) I’ve installed docker and followed these instructions. Here is my service file:
|
|
.include /usr/lib/systemd/system/docker.service
[Service]
# assume 192.168.1.1 is your proxy server, don't use 127.0.0.1
#Environment="http_proxy=192.168.1.1:3128"
ExecStart=
ExecStart=/usr/bin/docker -d -g /home/cyneox/work/docker
I’ve added myself to the docker group in order to be able to start docker as a regular user:
|
|
Afterwards make sure you enable the service:
|
|
Now make sure you do a reboot (Windows style :D).
|
|
836 ? Ssl 0:00 /usr/bin/docker -d -g /home/cyneox/work/docker
|
|
Containers: 0
Images: 0
Storage Driver: devicemapper
Pool Name: docker-8:1-385640-pool
Pool Blocksize: 64 Kb
Data file: /home/cyneox/work/docker/devicemapper/devicemapper/data
Metadata file: /home/cyneox/work/docker/devicemapper/devicemapper/metadata
Data Space Used: 291.5 Mb
Data Space Total: 102400.0 Mb
Metadata Space Used: 0.7 Mb
Metadata Space Total: 2048.0 Mb
Execution Driver: native-0.2
Kernel Version: 3.16.1-1-ARCH
Operating System: Arch Linux
WARNING: No swap limit support
Install Androguard
I could find 3 maintained dockerized Android images:
- https://github.com/adepasquale/docker-androguard
- https://github.com/dweinstein/dockerfile-androguard
- https://github.com/aikinci/androguard
The 2nd one started automatically androguard so you couldn’t tweak the underlying system. So I’ve decided to look at @aikinci’s androguard docker container.
|
|
Unable to find image 'honeynet/androguard' locally
Pulling repository honeynet/androguard
[1B
[0B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[1B
[36B]0;root@de3fbe90bdde: ~root@de3fbe90bdde:~# ^C
]0;root@de3fbe90bdde: ~root@de3fbe90bdde:~#
]0;root@de3fbe90bdde: ~root@de3fbe90bdde:~#
It must say that was pretty fast. And easy to do! In the end you’ll get a root bash prompt. Since the image does not provide all the tools I need, you’ll have to install them manually. After you have exited from the container you can attach it again. But first lets see which container are currently active:
|
|
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
de3fbe90bdde honeynet/androguard:latest "/bin/bash" 5 minutes ago Up 5 minutes sleepy_lalande
Now you can re-attach to a specific container by using docker attach:
|
|
Now I’ve installed some additional packages:
|
|
Now change the root password:
|
|
Start SSH server:
|
|
Now most important: You’ll have to commit your change to the image otherwise all changes will be lost on next start. On the maching running docker run:
|
|
Network with docker
When started docker creates a new virtual interface on the host machine called docker0 (more):
|
|
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.42.1 netmask 255.255.0.0 broadcast 0.0.0.0
inet6 fe80::bd01:3011:3b12:b866 prefixlen 64 scopeid 0x20<link>
ether 56:84:7a:fe:97:99 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
As you can see docker choosed a subnet and assigned an IP address to that interface. What about the guest machine?
|
|
Can I reach the container within the host machine?
|
|
PING 172.17.0.2 (172.17.0.2) 56(84) bytes of data.
64 bytes from 172.17.0.2: icmp_seq=1 ttl=64 time=0.086 ms
64 bytes from 172.17.0.2: icmp_seq=2 ttl=64 time=0.118 ms
64 bytes from 172.17.0.2: icmp_seq=3 ttl=64 time=0.131 ms
64 bytes from 172.17.0.2: icmp_seq=4 ttl=64 time=0.099 ms
--- 172.17.0.2 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 2997ms
rtt min/avg/max/mdev = 0.086/0.108/0.131/0.020 ms
Looks good! Well before I go to the next steps let me show my current pentest setup.
Pentest setup
|
|
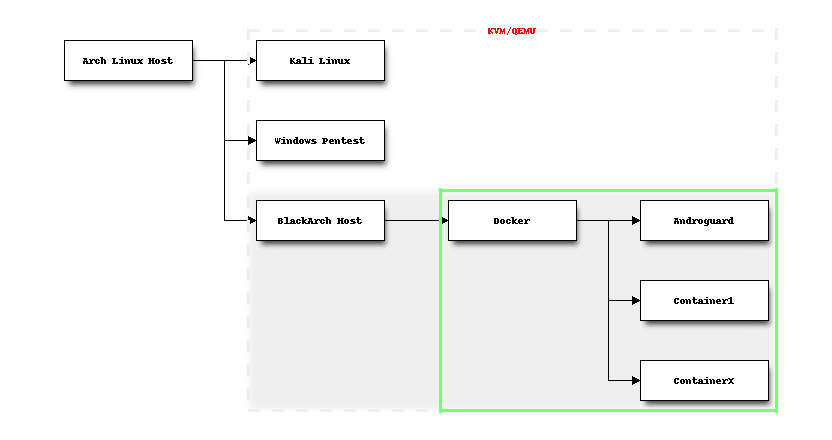
On my physical machine (Arch Linux Host) I run several QEMU instances:
- Kali Linux (Pentest)
- Windows (Pentest)
- BlackArch (Pentest)
A little bit of networking
Inside BlackArch I run docker which manages several containers. Regarding the networking part this is what I want to achieve:
- Be able to access
AndroguardfromArch Linux Host - Be able to access
AndroguardfromBlackArch Host - Be able to access the Internet from
Androguard
The first one is the most important to me, since I want to access the Androguard container directly - preferably through SSH. Since the Àndroguard machine gets a private IP address, it’s obvious I can’t access it - yet. The packets must be routed though BlackArch Host. Let’s check IPv4 forwarding:
|
|
net.ipv4.conf.all.forwarding = 1
Ok for now. The Docker documentation states:
By default Docker containers can make connections to the outside world, but the outside world cannot connect to containers. Each outgoing connection will appear to originate from one of the host machine’s own IP addresses thanks to an iptables masquerading rule on the host machine that the Docker server creates when it starts
After starting the Androguard container, let’s check the firewall rules:
|
|
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DOCKER all -- anywhere anywhere ADDRTYPE match dst-type LOCAL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
DOCKER all -- anywhere !127.0.0.0/8 ADDRTYPE match dst-type LOCAL
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- localhost/16 anywhere
Chain DOCKER (2 references)
target prot opt source destination
Having a futher look at the documentaton, I’ve found this:
More convenient is the -p SPEC or –publish=SPEC option which lets you be explicit about exactly which external port on the Docker server — which can be any port at all, not just those in the 49000–49900 block — you want mapped to which port in the container.
Now, let’s stop the container and restart it again with the -p paramater:
|
|
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
534dc09cc451 honeynet/androguard:latest "/bin/bash" 14 seconds ago Exited (0) 8 seconds ago sleepy_mcclintock
|
|
534dc09cc451
534dc09cc451
|
|
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
|
]0;root@469eced649c1: ~root@469eced649c1:~# ^C
]0;root@469eced649c1: ~root@469eced649c1:~#
]0;root@469eced649c1: ~root@469eced649c1:~#
Now let’s check iptables again:
|
|
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DOCKER all -- anywhere anywhere ADDRTYPE match dst-type LOCAL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
DOCKER all -- anywhere !127.0.0.0/8 ADDRTYPE match dst-type LOCAL
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- localhost/16 anywhere
Chain DOCKER (2 references)
target prot opt source destination
DNAT tcp -- anywhere anywhere tcp dpt:49154 to:172.17.0.4:22
As you can see in the last line all packets sent to localhost:49154 (which is BlackArch Host) will be forwarded to 172.17.0.4:22. Bingo! On Arch Linux Host I try to reach Androguard:
|
|
Perfect!
Accessing IPython on Androguard
Now you could use port forwarding to access services on Androguard through the SSH tunnel. On the Androguard machine I usually start ipython-notebook to take notes etc. I usually run it as:
|
|
On ArchLinux Host I run:
|
|
As you can see I’ve successfully logged in into the Androguard machine through BlackArch Host using DNAT. On ArchLinux Host I can open the browser and point to http://localhost:7777 which connects to IPython on the Androguard machine.