usd AG has announced a hacking challenge I have participated at. The target system was available at http://82.195.79.41/. Now let me sum up thg steps that have been required in order to get all 6 tokens.
|
|
Scratch the surface #
Let’s first conduct a nmap scan to see which ports are open.
|
|
Starting Nmap 6.47 ( http://nmap.org ) at 2015-03-18 20:57 CET
Nmap scan report for 82.195.79.41
Host is up (0.053s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
| http-robots.txt: 2 disallowed entries
|_/no/one/will/ever/know/ /~freddy/
|_http-title: usd Hackertag Challenge Website
7777/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c6:62:55:12:32:5d:d9:15:bc:1e:51:77:0e:5a:96:ea (RSA)
|_ 256 22:f9:96:0c:2e:99:11:17:d0:a8:89:41:40:b6:3d:58 (ECDSA)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.70 seconds
So we have 2 disallowed entries. Let’s have a look:
|
|
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<title>Index of /no/one/will/ever/know</title>
</head>
<body>
<h1>Index of /no/one/will/ever/know</h1>
<table><tr><th><img src="/icons/blank.gif" alt="[ICO]"></th><th><a href="?C=N;O=D">Name</a></th><th><a href="?C=M;O=A">Last modified</a></th><th><a href="?C=S;O=A">Size</a></th><th><a href="?C=D;O=A">Description</a></th></tr><tr><th colspan="5"><hr></th></tr>
<tr><td valign="top"><img src="/icons/back.gif" alt="[DIR]"></td><td><a href="/no/one/will/ever/">Parent Directory</a></td><td> </td><td align="right"> - </td><td> </td></tr>
<tr><td valign="top"><img src="/icons/text.gif" alt="[TXT]"></td><td><a href="secret.txt">secret.txt</a></td><td align="right">04-Mar-2015 15:23 </td><td align="right"> 14 </td><td> </td></tr>
<tr><th colspan="5"><hr></th></tr>
</table>
</body></html>
First token #
If you pay attention you’ll see a secret.txt in that directory:
|
|
Token: 928191
Bingo! Ok what about ~freddy:
|
|
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<title>Index of /~freddy</title>
</head>
<body>
<h1>Index of /~freddy</h1>
<table><tr><th><img src="/icons/blank.gif" alt="[ICO]"></th><th><a href="?C=N;O=D">Name</a></th><th><a href="?C=M;O=A">Last modified</a></th><th><a href="?C=S;O=A">Size</a></th><th><a href="?C=D;O=A">Description</a></th></tr><tr><th colspan="5"><hr></th></tr>
<tr><td valign="top"><img src="/icons/back.gif" alt="[DIR]"></td><td><a href="/">Parent Directory</a></td><td> </td><td align="right"> - </td><td> </td></tr>
<tr><th colspan="5"><hr></th></tr>
</table>
</body></html>
OK, nothing to see here. BUT: We keep in mind that freddy is probably a local username.
2nd token #
The nmap results suggested that there is a HTTPD on port 80. Let’s see what nikto finds:
|
|
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 82.195.79.41
+ Target Hostname: 82.195.79.41
+ Target Port: 80
+ Start Time: 2015-03-18 20:07:20 (GMT1)
---------------------------------------------------------------------------
+ Server: Apache
+ Uncommon header 'x-frame-options' found, with contents: sameorigin
+ Server leaks inodes via ETags, header found with file /robots.txt, inode: 131873, size: 68, mtime: 0x511175d9c5600
+ OSVDB-3268: /no/one/will/ever/know/: Directory indexing found.
+ File/dir '/no/one/will/ever/know/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /~freddy/: Directory indexing found.
+ File/dir '/~freddy/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-3092: /.svn/entries: Subversion Entries file may contain directory listing information.
+ OSVDB-3092: /.svn/wc.db: Subversion SQLite DB file may contain directory listing information.
+ 6545 items checked: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2015-03-18 20:19:17 (GMT1) (717 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Besides thet robots.txt entries .svn looks very interesting. Let’s have a closer look:
|
|
|
|
| local_relpath | checksum | |
|---|---|---|
| 0 | download.php | $sha1$71d7c4326159dff73464c31c8b8f3ee0aad3a805 |
| 1 | None |
Obviously there is a download.php which we can retrieve from the SVN repo. Using the tutorial one can access the files inside the repository very easily:
|
|
<?php
include "src/header.php";
// Todo: Challenge fuer Token 102342 bauen.
echo '
<div id="contentliquid"><div id="content">
<p>Die folgende Datei steht zum Download bereit:</p>
<ul>
<li><a href="dl/usd_Hackertag_2015.pdf">usd Hackertag Poster (PDF-Format)</a></li>
</ul>
';
echo "</div></div>";
include "src/menu.php";
include "src/footer.php";
?>
There is this line:
Todo: Challenge fuer Token 102342 bauen.
3rd Token #
Now let’s have a look at the PDF under http://82.195.79.41/download.php.
|
|
usd_Hackertag_2015.pdf: PDF document, version 1.3
When you look at it (PDF viewer) nothing special about it.
Let’s extract all available strings:
|
|
/ModDate (D:20150220100358+01'00')
/Producer (Adobe PDF library 10.01)
/Title (usd Hackertag 2015)
/Trapped /False
/Subject (Token: 338912)
endobj
xref
0000000000 65535 f
0000608444 00000 n
0000651051 00000 n
trailer
/Size 44
/Root 6 0 R
/Info 4 0 R
/ID [ <B86554FD3FAA6D459E2C0B3D46980BDB> <f302C8F15AC3244B86122640F6B03D76> ]
/Prev 116
%EndExifToolUpdate 608422
startxref
651378
%%EOF
Again bingo: Token: 338912
4th Token #
Now let’s have a look at the main web-page. Somewhere you’ll see this line:
|
|
But wait a sec. JQuery? That sounds suspicious.
|
|
eval(String.fromCharCode(105, 102, 32, 40, 119, 105, 110, 100, 111, 119, 46, 108, 111, 99, 97, 116, 105, 111, 110, 46, 104, 111, 115, 116, 110, 97, 109, 101, 32, 61, 61, 32, 34, 49, 50, 55, 46, 48, 46, 48, 46, 49, 34, 41, 32, 123, 10, 118, 97, 114, 32, 95, 48, 120, 98, 55, 57, 97, 61, 91, 34, 92, 120, 53, 55, 92, 120, 54, 57, 92, 120, 54, 67, 92, 120, 54, 67, 92, 120, 54, 66, 92, 120, 54, 70, 92, 120, 54, 68, 92, 120, 54, 68, 92, 120, 54, 53, 92, 120, 54, 69, 92, 120, 50, 48, 92, 120, 55, 65, 92, 120, 55, 53, 92, 120, 55, 50, 92, 120, 70, 67, 92, 120, 54, 51, 92, 120, 54, 66, 92, 120, 50, 48, 92, 120, 54, 54, 92, 120, 55, 50, 92, 120, 54, 53, 92, 120, 54, 52, 92, 120, 54, 52, 92, 120, 55, 57, 92, 120, 50, 69, 92, 120, 50, 48, 92, 120, 52, 52, 92, 120, 54, 53, 92, 120, 55, 50, 92, 120, 50, 48, 92, 120, 54, 55, 92, 120, 54, 53, 92, 120, 54, 56, 92, 120, 54, 53, 92, 120, 54, 57, 92, 120, 54, 68, 92, 120, 54, 53, 92, 120, 50, 48, 92, 120, 53, 52, 92, 120, 54, 70, 92, 120, 54, 66, 92, 120, 54, 53, 92, 120, 54, 69, 92, 120, 50, 48, 92, 120, 54, 67, 92, 120, 54, 49, 92, 120, 55, 53, 92, 120, 55, 52, 92, 120, 54, 53, 92, 120, 55, 52, 92, 120, 51, 65, 92, 120, 50, 48, 92, 120, 51, 52, 92, 120, 51, 49, 92, 120, 51, 55, 92, 120, 51, 56, 92, 120, 51, 53, 92, 120, 51, 53, 34, 93, 59, 97, 108, 101, 114, 116, 40, 95, 48, 120, 98, 55, 57, 97, 91, 48, 93, 41, 59, 10, 125));
|
|
|
|
'if (window.location.hostname == "127.0.0.1") {\nvar _0xb79a=["\\x57\\x69\\x6C\\x6C\\x6B\\x6F\\x6D\\x6D\\x65\\x6E\\x20\\x7A\\x75\\x72\\xFC\\x63\\x6B\\x20\\x66\\x72\\x65\\x64\\x64\\x79\\x2E\\x20\\x44\\x65\\x72\\x20\\x67\\x65\\x68\\x65\\x69\\x6D\\x65\\x20\\x54\\x6F\\x6B\\x65\\x6E\\x20\\x6C\\x61\\x75\\x74\\x65\\x74\\x3A\\x20\\x34\\x31\\x37\\x38\\x35\\x35"];alert(_0xb79a[0]);\n}'
|
|
b'Willkommen zur\xfcck freddy. Der geheime Token lautet: 417855'
Our found token: 417855
5th Token #
I must say this part of the challenge was the most “challenging” one. The found vulnerability was actually obvious but it took me to long to exploit it :D But first a short introduction to the vulnerability itself.
There was this link http://82.195.79.41/liste.php?id=1 which caught my attention from the beginning.
The first thing I did:
|
|
<div id="contentliquid"><div id="content">unrecognized token: "'1'';"
Aha.. Ok. Let’s try again:
|
|
<div id="contentliquid"><div id="content">unrecognized token: "';"
What about the next one?
|
|
<div id="contentliquid"><div id="content"><ul><li><a href="/liste.php?id=a">k</a><ul></div></div>
<div id="leftcolumn">
<ul>
<li><a href="http://82.195.79.41/index.php">Startseite</a></li>
<li><a href="http://82.195.79.41/liste.php">Todo-Liste</a></li>
<li><a href="http://82.195.79.41/restricted/index.php">Backend</a></li>
<li><a href="http://82.195.79.41/download.php">Downloads</a></li>
<li><a href="http://www.usd.de/impressum/" target="_blank">Impressum</a></li>
<li><a href="http://www.usd.de/datenschutz/" target="_blank">Datenschutz</a></li>
</ul>
</div>
<div id="footer">
<p></p>
</div>
</div>
</body>
</html>
Have you noticed this line?
|
|
a and b were successfully “merged” into the results. Now the biggest problem I had was the fingerprinting of the DB itself. OWASP has sth you can use in your tests. But the most useful thing is to test for string concatenation (nice article here). So I’ve tried several things:
|
|
<div id="contentliquid"><div id="content">unrecognized token: "';"
|
|
<div id="contentliquid"><div id="content"><ul><li><a href="/liste.php?id=a">k</a><ul></div></div>
|
|
<div id="contentliquid"><div id="content"><ul><li><a href="/liste.php?id=ab">k</a><ul></div></div>
Well 'a'||'b' seemed to work. That syntax is Oracle specific. But also SQLite specific. And this was my biggest mistake: I was searching for Oracle specific injections, but the DBMS was in fact SQLite. Finally I’ve constructed this query:
|
|
<div id="contentliquid"><div id="content"><ul><li><a href="/liste.php?id=a">token</a><li><a href="/liste.php?id=a">public</a><ul></div></div>
So there are 2 tables available:
- token
- public
Let’s have a look at the schema of token:
|
|
<div id="contentliquid"><div id="content"><ul><li><a href="/liste.php?id=a">CREATE TABLE token (token_val NUMERIC)</a><ul></div></div>
Ok, now go for it:
|
|
<div id="contentliquid"><div id="content"><ul><li><a href="/liste.php?id=a">336809</a><ul></div></div>
Token 336809 is the next one.
6th and last Token #
While looking for tokens, I have seen this message a couple of times:
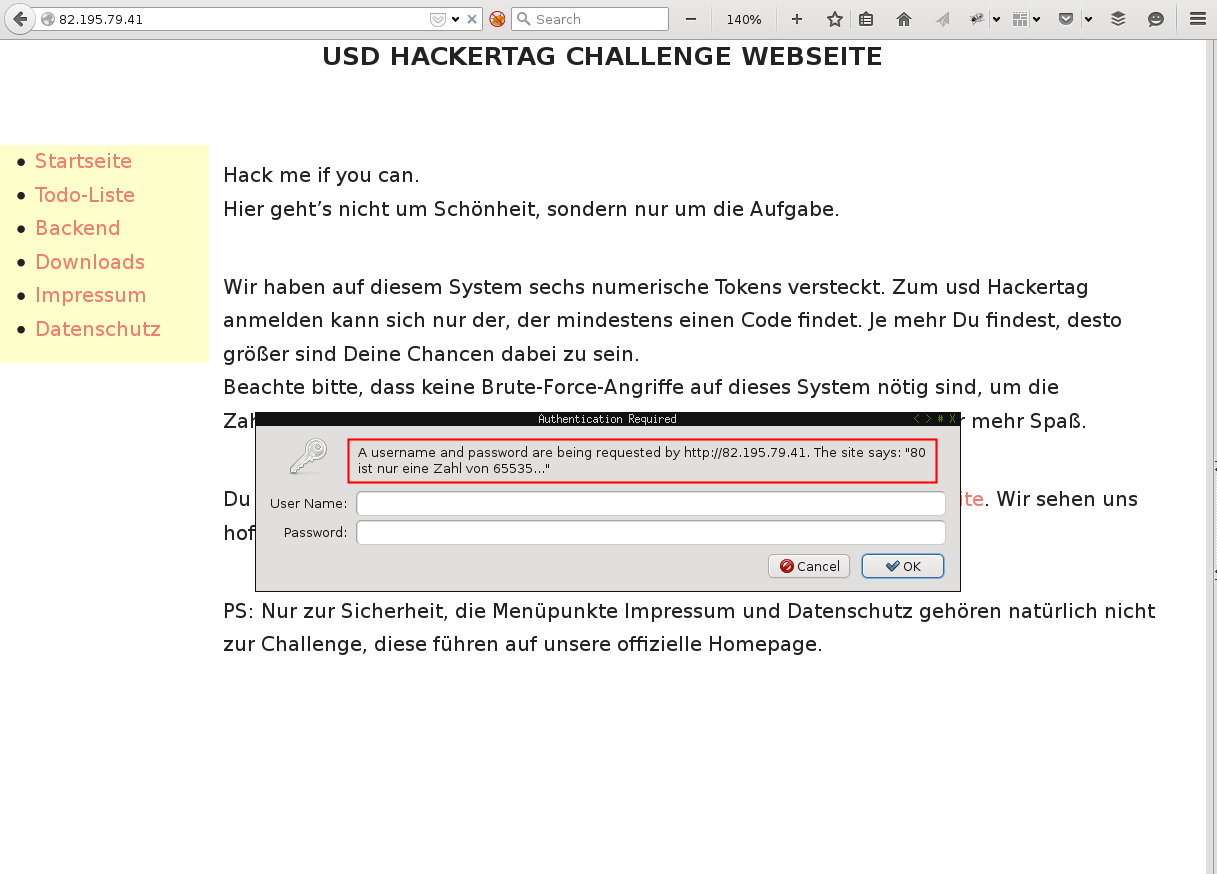
The realm says: 80 is just a number of 65535. Ok hat was a hint for more undetected ports. I’ve run nmap again:
|
|
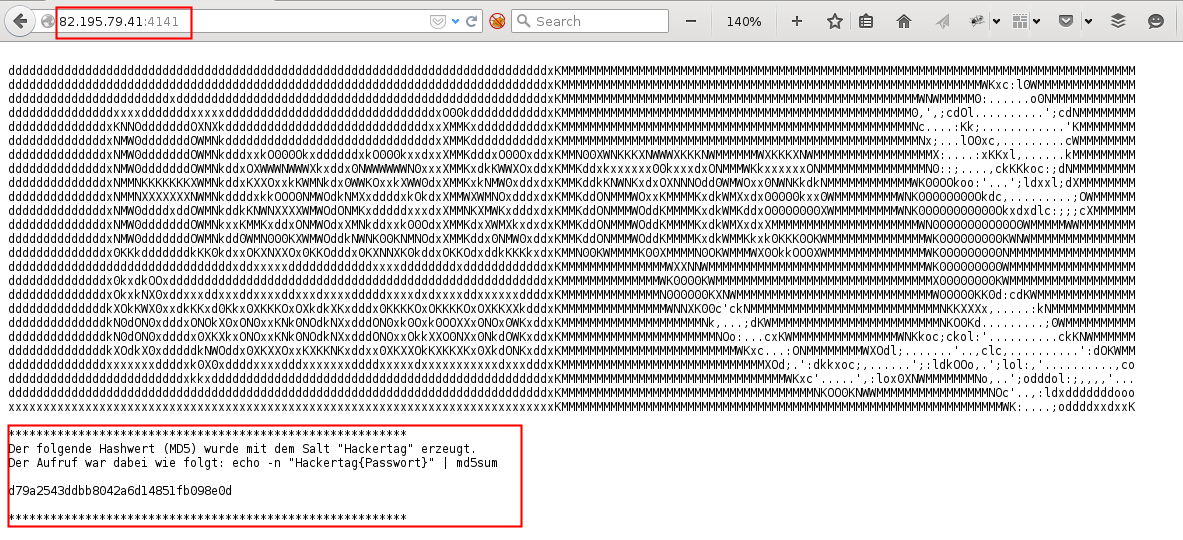
OH! What’s behind port 4141?
|
|
dddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
dddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWKxc:l0WMMMMMMMMMMMMMM
dddddddddddddddddddddddxdddddddddddddddddddddddddddddddddddddddddddddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWNWMMMMM0:......o0NMMMMMMMMMMMM
dddddddddddddddxxxxdddddddxxxxxddddddddddddddddddddddddddddddxO00kdddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM0,',;cdOl..........';cdNMMMMMMMM
ddddddddddddddxKNNOdddddddOXNXkdddddddddddddddddddddddddddddxxXMMKxddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMNc....:Kk;............'KMMMMMMMM
ddddddddddddddxNMW0dddddddOWMNkddddddddddddddddddddddddddddddxXMMKdddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMNx;...lO0xc,.........cWMMMMMMMM
ddddddddddddddxNMW0dddddddOWMNkdddxxkO000OkxddddddxkO000kxxdxxXMMKdddxO00OxddxKMMN00XWNKKKXNWWWXKKKNWMMMMMMWXKKKXNWMMMMMMMMMMMMMMMMMX:....:xKKxl,......kMMMMMMMMM
ddddddddddddddxNMW0dddddddOWMNkddxOXWWWNWWWXkxddx0NWWWWWWN0xxxXMMKxdkKWWXOxddxKMMKddxkxxxxxx00kxxxdxONMMMWKkxxxxxxONMMMMMMMMMMMMMMMN0::;....,ckKKkoc:;dNMMMMMMMMM
ddddddddddddddxNMMNKKKKKKKXWMNkddxKXXOxxkKWMNkdx0WWKOxxkXWW0dxXMMKxkNMW0xddxdxKMMKddkKNWNKxdxOXNNNOdd0WMWOxx0NWNKkdkNMMMMMMMMMMMMWK00OOkoo:'...';ldxxl;dXMMMMMMMM
ddddddddddddddxNMMNXXXXXXXNWMNkddddxkkOOO0NMWOdkNMXxddddxkOkdxXMMWXWMNOxdddxdxKMMKddONMMMWOxxKMMMMKxdkWMXxdx00000kxx0WMMMMMMMMMWNK00000000Okdc,.........;OWMMMMMM
ddddddddddddddxNMW0ddddxddOWMNkddkKNWNXXXXWMWOdONMKxdddddxxxdxXMMNKXMWKxdddxdxKMMKddONMMMWOddKMMMMKxdkWMKddxO0000000XWMMMMMMMMMWNK00000000000Okxdxdlc:;;;cXMMMMMM
ddddddddddddddxNMW0dddddddOWMNkxxKMMKxddxONMWOdxXMNkddxxk00OdxXMMKdxXWMXkxdxdxKMMKddONMMMWOddKMMMMKxdkWMXxdxXMMMMMMMMMMMMMMMMMMMMMWN00000000O00O0WMMMMMWWMMMMMMMM
ddddddddddddddxNMW0dddddddOWMNkdd0WMN000KXWMWOddkNWNK00KNMNOdxXMMKddx0NMW0xddxKMMKddONMMMWOddKMMMMKxdkWMMKkxk0KKK0OKWMMMMMMMMMMMMMMWK000000000KWNWMMMMMMMMMMMMMMM
ddddddddddddddx0KKkdddddddkKK0kdxxOKXNXXOx0KKOdddx0KXNNXK0kddxOKKOdxddkKKKkxdxKMMN00KWMMMMK00XMMMMN0OKWMMMWX0OkkOO0XWMMMMMMMMMMMMMMWK000000000NMMMMMMMMMMMMMMMMMM
ddddddddddddddddddddddddddddddddxddxxxxxddddddddddddxxxxddddddddxddddddddddddxKMMMMMMMMMMMMMMMWXXNNWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWK000000000WMMMMMMMMMMMMMMMMMM
ddddddddddddddx0kxdkOOxddddddddddddddddddddddddddddddddddddddddddddddddddddddxKMMMMMMMMMMMMMMWK0000KWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMX00000000KWMMMMMMMMMMMMMMMMMM
ddddddddddddddxOkxkNX0xddxxxddxxxddxxxxddxxxdxxxxdddddxxxxdxdxxxxddxxxxxxddddxKMMMMMMMMMMMMMMN000000KXNWMMMMMMMMMMMMMMMMMMMMMMMMMMMMW00000KK0d:cdKWMMMMMMMMMMMMMM
ddddddddddddddkXOkKWX0xxdkKKxd0Kkx0XKKKOxOXkdkXKxdddx0KKKKOxOKKKKOxOXKKXXkdddxKMMMMMMMMMMMMMMMWNNXK00c'ckNMMMMMMMMMMMMMMMMMMMMMMMMMMMNKKXXXx,.....:kNMMMMMMMMMMMM
ddddddddddddddkN0dON0xdddxONOkX0xON0xxKNk0NOdkNXxdddON0xk0Oxk0OOXXx0NOx0WKxddxKMMMMMMMMMMMMMMMMMMMMNk,...;dKWMMMMMMMMMMMMMMMMMMMMMMMMNKO0Kd.........;0WMMMMMMMMMM
ddddddddddddddkN0dON0xddddx0XKXkxONOxxKNk0NOdkNXxdddONOxxOkkXXO0NXx0NkdOWKxddxKMMMMMMMMMMMMMMMMMMMMMMNOo:...cxKWMMMMMMMMMMMMMMMWNKkoc;ckol:'..........ckKNWMMMMMM
ddddddddddddddkXOdkX0xdddddkNWOddx0XKXXOxxKXKKNKxddxx0XKXXOkKXKKXKx0XkdONKxddxKMMMMMMMMMMMMMMMMMMMMMMMMMWKxc...:ONMMMMMMMMWXOdl;.......'..,clc,..........':dOKWMM
ddddddddddddddxxxxxxxddddxk0X0xddddxxxxdddxxxxxxxddddxxxxxdxxxxxxxxxxxdxxxdddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMXOd;.':dkkxoc;,......';:ldkOOo,.';lol:,'..........,co
dddddddddddddddddddddddddxkkxddddddddddddddddddddddddddddddddddddddddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWKxc'.....',:lox0XNWMMMMMMMNo,..';odddol:;,,,,'...
dddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMNKOO0KNWWMMMMMMMMMMMMMMMMNOc'..,:ldxdddddddooo
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWK:....;oddddxxdxxK
*********************************************************
Der folgende Hashwert (MD5) wurde mit dem Salt "Hackertag" erzeugt.
Der Aufruf war dabei wie folgt: echo -n "Hackertag{Passwort}" | md5sum
d79a2543ddbb8042a6d14851fb098e0d
*********************************************************
What it basically says, is that a certain MD5 hash was created using echo -n "Hackertag{Password}", where Hackertag is a salt. And given the hash I should find out the right password. I have never used hashcat before but this was the right time to do it. After reading some docs, I was able to get the right password in ca. 3 seconds :)
|
|
Initializing hashcat v0.49 with 2 threads and 32mb segment-size...
Added hashes from file hash: 1 (1 salts)
Activating quick-digest mode for single-hash
NOTE: press enter for status-screen
Input.Mode: Mask (H) [1]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Ha) [2]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hac) [3]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hack) [4]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hacke) [5]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hacker) [6]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hackert) [7]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hackerta) [8]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hackertag) [9]
Index.....: 0/1 (segment), 1 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 1/1 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hackertag?l) [10]
Index.....: 0/1 (segment), 26 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 26/26 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hackertag?l?l) [11]
Index.....: 0/1 (segment), 676 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 676/676 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Input.Mode: Mask (Hackertag?l?l?l) [12]
Index.....: 0/1 (segment), 17576 (words), 0 (bytes)
Recovered.: 0/1 hashes, 0/1 salts
Speed/sec.: - plains, - words
Progress..: 17576/17576 (100.00%)
Running...: --:--:--:--
Estimated.: --:--:--:--
d79a2543ddbb8042a6d14851fb098e0d:Hackertagblue
All hashes have been recovered
Input.Mode: Mask (Hackertag?l?l?l?l) [13]
Index.....: 0/1 (segment), 456976 (words), 0 (bytes)
Recovered.: 1/1 hashes, 1/1 salts
Speed/sec.: - plains, 5.03M words
Progress..: 296192/456976 (64.82%)
Running...: --:--:--:--
Estimated.: --:--:--:--
Started: Wed Mar 18 21:45:47 2015
Stopped: Wed Mar 18 21:45:47 2015
We can verify that:
|
|
d79a2543ddbb8042a6d14851fb098e0d -
Perfect! Now we can use the passwort to access this link: http://82.195.79.41/restricted/index.php. Inside you’ll see a image and nothing more:
But again let’s have a look at the image itself:
|
|
VG9rZW46IDU1MTI0Mw==
That looks interesting:
|
|
Token: 551243
That’s it! :)
